While going through the post on cloning in GitHub, I realized that I used a link that appears when we press the Clone or download button, to clone the repository. However, observing closely, one might notice the caption of the popup. For those who missed it, let me show it. The pop-up after pressing the button looked like this for the repository ToolsQA.
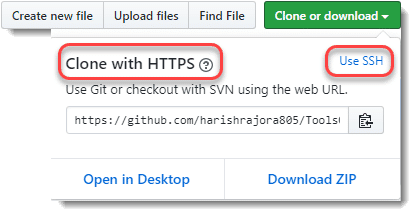
There are two options to clone as can be seen in the image.
- Cloning a GitHub repository with HTTPS.
- Cloning a GitHub repository using SSH.
In the same post, I mentioned that we will use ssh in the later tutorials. Well, the time has come. SSH and HTTPS are the two ways to clone a repository from GitHub. In general, SSH and HTTPS are the two major types of protocols that internet communication all over the world uses. While HTTPS is a straightforward way, SSH contains some setup overhead. Both of these have their pros and cons, and we will discuss the same in the subsequent sections. But, before using SSH, let's introduce HTTPS briefly.
HTTPS protocol in GitHub operations
HTTPS is a secure communication protocol. Using HTTPS protocol, any two machines, be it a server or a client, can communicate securely over the network HTTPS ensures security by encrypting the data transferred over the transport layer of the network. HTTPS has become very popular since its introduction. Additionally, websites over the internet use it heavily. As shown in the above screenshot, when a user goes for cloning of a repository on GitHub, the default option provided by GitHub is "Clone with HTTPS" and it might seem like that GitHub prefers HTTPS over SSH. But, this cannot and should not claim although there have been some indications in the past.
Does GitHub recommend using HTTPS?
Long back, the following link about generating ssh keys on GitHub used to state and quote - If you have decided not to use the recommended HTTPS method, we can use SSH keys to establish a secure connection between your computer and GitHub. The steps explained below will take you through generating an SSH key and then adding the public key to your GitHub account. It is around the time when GitHub was launched and new to the world. Further, they changed their statement on the same page states that We strongly recommend using an SSH connection when interacting with GitHub. At the current time, they clearly recommend HTTPS protocol to use for cloning. It is not available on the same link but on a new link which remote URL should I use?
Cloning a GitHub repository using HTTPS
Once the user presses the clone or download button, GitHub shows the pop-up having the HTTPS URL link as the default option to clone a repository. The discussion on detailed steps of cloning a GitHub repository using HTTPS protocol has already happened in the post on how to clone in GitHub.
Advantages of using HTTPS protocol for Git operations
HTTPS protocol provides the following advantages when used during git operations:
- Easy to Use: HTTPS is easy to use. It was the main reason GitHub recommended it in the first place. To use HTTPS, the user has to copy the URL and run the git clone command to clone the repository. It is more comfortable and convenient to utilize for a user, especially for a beginner.
- FewerFirewall Restriction: HTTPS has minimal firewall restriction, and it is improbable that a firewall will block the communication over HTTPS. Also, all repositories use it, be it public or private, and it works even if you are behind a proxy server.
Disadvantages of Using HTTPS Protocol For Git Operations
HTTPS protocol has the following disadvantages when used during git operations:
-
Repetitive Authentication: Whenever the user performs the network-based communication of any type such as pushing the changes to the repository or pulling the changes, every time they need to enter the credentials to authenticate their actions. Since these actions happen many times in a day, repetitive prompts and entering the credentials sometimes irritate the users.
-
Configuring Credentials Manager: To avoid the above issue, few users install and configure utilities such as credentials managers or keychain to auto-populate the credentials. But, in this method, if the user has to change the password, they have to configure everything from scratch. Which, in turn, is a pain in itself. Fortunately, SSH saves us from all of this.
What is SSH Protocol in Git?
SSH or Secure Shell is a cryptographic network protocol used for communicating over the network. The usage of SSH protocol has increased a lot over time; some of its applications include remote login to a machine or controlling the terminal of a remote device. Although it's not confined and the applications are enormous in today's interconnected world. In the later tutorials, we will cover another application of SSH protocol briefing "how to authenticate a GitHub repository through SSH client". But first, let's see the pros of using SSH:
Advantages Of Using SSH Protocol For Git Operations
In this section, we will explore some pros of using SSH instead of HTTPS in Git.
SSH protocol provides the following advantages when used during git operations:
- No Repetitive Authentication: SSH removes the burden of authenticating on the remote server repeatedly for every action that you do. It is one of the significant reasons developers prefer SSH over HTTPS.
- Saves Time: Using SSH saves a lot of time since the user does not enter credentials every time.
- Secure: SSH keys are more secure than any password you can imagine. Even with million and trillion of permutations, it's almost impossible to crack an SSH key.
Disadvantages of Using SSH protocol for Git Operations
Although SSH boasts many pros, it also has certain disadvantages, which are as below:
- Set-Up Cost: The initial setup for SSH is a bit complicated and time-consuming. Which, in turn, leads to a higher cost. But it's just a one-time effort.
- Firewall restrictions: Firewalls and proxy servers generally restrict SSH communications. Explicit firewall exceptions need to be configured to allow communication over the SSH protocol, which also adds to additional work and cost.
The above details give a better understanding of why to use SSH instead of conventional HTTPS. Even though many developers still use HTTPS. Let's not forget that the user should use SSH only on those computers that they use regularly. While we will set up the SSH authentication in the following tutorial, it is essential to know two basic concepts that we will encounter. These are the heart of the SSH protocol, and we will be setting them up in the next tutorial.
Along with the HTTPS and SSH protocols, private and public keys are fundamental in cryptography. While authenticating through SSH, we will be generating both of them and verify our actions using them. In the next tutorial, we will set up SSH authentication and will try to push some changes through SSH.